Use allow and deny lists to generate or suppress anomalies
Add a domain or IP address to a deny list to generate anomalies whenever a user or device interacts with that domain or IP address.
- Interaction with a denied domain generates a Denylisted Domain anomaly.
- Interaction with a denied IP generates a Denylisted IP Address anomaly.
You can view the IP or domain, confidence rating, and source for a denied anomaly on the Anomaly details page.
Add a user, domain, or IP address to an allow list to prevent anomalies based on interactions with that user, domain, or IP address from being generated. Using an allow list prevents an anomaly from being created if the anomaly involves a single user. If an anomaly involves an allowed user and another user, it will still be generated. Add a user to an allow list if they are a penetration tester and you would expect anomalous or suspicious activity while they conduct their tests.
The allow list takes priority over the deny list. If a domain is on both lists, denied domain anomalies based on that domain are not generated.
What is denied or allowed in Splunk UBA?
This table shows what Splunk UBA denies and allows by default.
| Deny list or allow list | Description |
|---|---|
| Denied domains | Splunk UBA includes a list of high-confidence entries from the Collective Intelligence Framework (CIF). New entries are periodically added to the list in new versions of Splunk UBA. |
| Denied IP addresses | Splunk UBA does not include a default set of denied IP addresses. |
| Allowed domains | Splunk UBA selects allowed domains from the top 250,000 global website domain names according to Alexa. |
| Allowed IP addresses | Splunk UBA selects allowed IP addresses from the top 50,000 global website IP addresses and ranges according to Alexa. |
| Allowed users | Splunk UBA does not include a default set of allowed users. Add HR data to Splunk UBA before uploading a list of allowed users. |
Splunk UBA version 5.1.0 and higher no longer provides updates to the out-of-the-box popular domain list Alexa. Service provider Alexa is end of life.
How anomaly and threat models use deny lists and allow lists in Splunk UBA
This table shows the anomaly and threat models that interact with deny lists and allow lists in Splunk UBA. Any models not listed in the table do not have any interaction with deny lists or allow lists.
Click on the Model name column header to sort the table by model name, or click on the Model type column header to sort the table by model type.
| Model name | Model type | How this model uses allow lists | How this model uses deny lists |
|---|---|---|---|
| Suspicious Email Detection Model | Threat model | Checks if an email sender or recipient domain is on the allow list. Senders or recipient domains on the allow list are not automatically ignored and factor in to the threat's score and whether or not a threat is generated. | Checks if an email sender or recipient domain is on the deny list. Senders or recipient domains on the deny list are used as factors in determining whether or not a threat is generated. |
| Device Anomaly Ranking Task User Anomaly Ranking Task |
Produces risk rankings for users and devices based on their anomalies. | Checks if the anomaly contains entities on the allow list. Entities on the allow list can decrease an anomaly's score, or prevent an anomaly from being generated. | Checks if the anomaly contains entities on the deny list. Entities on the deny list can increase an anomaly's score. |
| Suspicious Data Movement Threat Model | Threat model | Checks if the destination of outgoing traffic is on the allow list. Destinations on the allow list can decrease a threat's score, or prevent a threat from being generated. | Checks if the destination of outgoing traffic is on the deny list. Destinations on the deny list can increase a threat's score. |
| Hypergraph-based Malware Threat Detection Model | Threat model | Checks if the activity involves domains on the allow list. Domains on the allow list can decrease an anomaly's score, or prevent an anomaly from being generated. | Checks if the activity involves domains on the deny list. Domains on the deny list can increase an anomaly's score. |
| External Alarm Analysis Model | Anomaly model | Checks if the activity involves domains on the allow list. Domains on the allow list can decrease an anomaly's score, or prevent an anomaly from being generated. | Checks if the activity involves domains on the deny list. Domains on the deny list can increase an anomaly's score. |
| Suspicious Data Transfer | Anomaly model | Not used. | Compares the country in the activity to a built-in list of countries on the deny list. Denylisted countries can increase the score of an anomaly. |
| IP Malware Communication Model | Anomaly Model | Destination IP addresses in the anomaly activity that are on the allow list are ignored. | Checks if the destination IP address is on the deny list. Destination IP addresses on the deny list can increase the score of an anomaly. |
| Malware Communication Model | Anomaly Model | Destination domains in the anomaly activity that are on the allow list are ignored. | Checks if the destination domain is on the deny list. Destination domains on the deny list can increase the score of an anomaly. |
| Browser Exploitation Model | Anomaly model | Destination domains in the anomaly activity that are on the allow list are ignored. | Checks if the destination domain is on the deny list. Denylisted domains on the deny list can increase the score of an anomaly. |
| Web Beaconing Detection Model | Anomaly model | Destination domains in the anomaly activity that are on the allow list are ignored.
|
Not used. |
| IP Beaconing Detection Model | Anomaly model | Destination IP addresses in the anomaly activity that are on the allow list are ignored. | Not used. |
| Rare User Agent String Model | Anomaly model | Destination domains in the anomaly activity that are on the allow list are ignored. | Not used. |
View deny lists and allow lists in Splunk UBA
View and modify existing or add new filter lists by selecting Manage > Deny/Allow Lists. Each list displays the total number of entries. Sort the list based on the domain, IP address, or username, source, confidence percentage, or the date reported. The date reported reflects the date that the entry was added to Splunk UBA.
Use the confidence percentage and the source to determine how much you can trust a list entry.
Add new entries to a deny list or allow list
You can add new entries to a deny or allow list by uploading a static file or by adding values using the Splunk UBA user interface.
Upload a static file
When adding new entries to a list by uploading a static file, the file must be a TXT file, with each entry on its own line.
Perform the following steps:
- In Splunk UBA, select Manage > Deny/Allow Lists.
- Select the list you want to add values to.
- Click Upload.
- Choose a List File from your computer.
- (Optional) Enter a comment describing the file you are uploading.
- Click OK.
Users are only added to the allow list if their user account already exists in Splunk UBA. Add HR data to Splunk UBA first before uploading a list of allowed users.
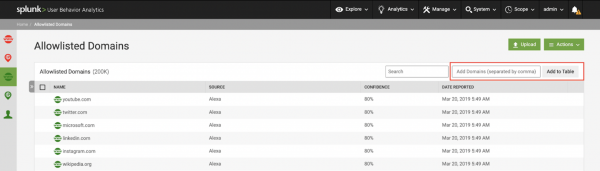
Manually add from the Splunk UBA user interface
Manual entry from the UI is available for Allowlisted Domains, Allowlisted IPs, Allowlisted Users, Denylisted Domains, and Denylisted IPs.
For large volumes of entries the static file upload option is faster.
- In Splunk UBA, select Manage > Deny/Allow Lists.
- Select the list you want to add values to.
- Add values to the input field. Values must be separated by commas.
- Click Add to Table.
Users are only added to the allow list if their user account already exists in Splunk UBA. Add HR data to Splunk UBA first before uploading a list of allowed users.
Remove entries from a deny list or allow list
You can remove individual list entries, or delete any file-based list sources.
Remove individual list entries
Remove individual list entries if you determine they are no longer needed or relevant.
- In Splunk UBA, select Manage > Deny/Allow Lists.
- Select the list from which you want to remove entries.
- Check the checkbox next to the entries you want to remove.
- Select Action > Delete.
- Click OK to confirm that you want to delete the selected entries.
Delete or disable list entries by source
Deleting or disabling a source removes all the list entries associated with a specific source.
- In Splunk UBA, select Manage > Deny/Allow Lists.
- Select the list from which you want to remove a source.
- Click Source to see the list entries sorted by source.
- Check the checkbox next to the source you want to remove.
- Select Action > Delete.
- Click OK to confirm that you want to delete the selected source.
If you delete an individual entry from a list, then disable the list from source, then enable the list, previously-deleted individual entries return to the list.
Use anomaly action rules if anomalies for allowed entities are still being generated
In some cases, you might see an anomaly generated against an allowed entity such as an IP address. To suppress anomalies from being generated against this entity, perform the following tasks:
- Create a new device watchlist.
- Add devices to the new watchlist.
- Use the watchlist in an anomaly action rule.
In the following example, we will suppress anomaly generation for the IP address 10.1.1.8.
Create a new device watchlist
First, perform the following tasks to create a new device watchlist:
- In Splunk UBA, select Manage > Watchlists.
- In the list of watchlist types, select Device Watchlists.
- Click New Watchlist.
- In the New Device Watchlist window, enter the watchlist name Allowlisted Devices.
- Click OK.
See Investigate Splunk UBA entities using watchlists in Use Splunk User Behavior Analytics for more information about Splunk UBA watchlists.
Add devices to the new watchlist
Add the IP address 10.1.1.8 to the Allowlisted Devices watchlist:
- In Splunk UBA, select Explore > Devices or click Devices on the home page.
- Enter 10.1.1.8 in the search field to locate this device.
- Click on the device to access the Device Details page.
- In the Watchlist field, click the star icon and then select Allowlisted Devices to add this device to the selected watchlist.
Use the watchlist in an anomaly action rule
Use the watchlist in an anomaly action rule. In this example, any anomaly containing an IP address in the Allowlisted Devices watchlist is moved to the trash and not generated:
- In Splunk UBA, select Explore > Anomalies or click Anomalies on the home page.
- Click the gear icon and verify that Anomaly Action Rules is selected.
- Click New Anomaly Action Rule.
- Conflgure the rule action:
- Click Delete Anomalies and Move to Trash as the rule action.
- Click Apply to Future and Existing Anomalies as the rule scope.
- Click Next.
- Configure the anomaly filters:
- Select Device Watchlists from the list of filters, then select the Allowlisted Devices watchlist.
- Set the additional filter options to Include and Contains Any.
- Click Next.
- Enter Do not generate anomalies against allowlisted devices as the rule name.
- (Optional) Enter a description for this rule.
- Click OK.
See Take action on anomalies with anomaly action rules in Administer Splunk User Behavior Analytics for more information about anomaly action rules.
| Exclude identity resolution for devices or users | Add Windows events to Splunk UBA |
This documentation applies to the following versions of Splunk® User Behavior Analytics: 5.2.0, 5.2.1, 5.3.0, 5.4.0, 5.4.1, 5.4.1.1, 5.4.2, 5.4.3
 Download manual
Download manual
Feedback submitted, thanks!